Cascaded liquid crystal holography for optical encryption
1. Introduction
The importance of information security has reached an unprecedented level in the wake of rapid advancements in information technology[1–3]. Significant efforts have been devoted to finding new encryption technologies to improve information security[4–6]. Optical holography has emerged as a crucial tool due to its ability to provide high-level security and protection for sensitive data[7–9]. In particular, geometric metasurfaces comprising nanostructured meta-atoms with versatile degrees of freedom supply extraordinary holographic functionalities that are unachievable by ordinary diffractive optics[10–13]. They can encode the information[14] in a single element by leveraging a range of light parameters, including the wavelength[15,16], amplitude[17], orbital angular momentum[18–20], polarization[21,22], etc. To further enhance the security, secret-sharing optical encryption method is implemented with cascaded metasurfaces, whereby the secret is split into multiple shares[23–25]. The enciphered message can only be unveiled with requisite secret keys that are appropriately stacked. Under this arrangement, the stolen secret share will not reveal the secret information. Despite impressive advancements in metaholographic encryption, there still remain some challenging issues, especially easy fabrication and dynamic tunability.
As a typical class of soft building blocks[26,27], liquid crystals (LCs) play a vital role in various electro-optical applications due to their unique anisotropic properties and sensitivity to diverse external stimuli[28–31]. Recently, LC holography that can manipulate the light field in the far field has attracted considerable attention[31–38], showing the merits of easy fabrication, dynamic tunability, high flexibility, high efficiency, and compact geometry[39–42]. For instance, multifunctional LC holographic devices have been demonstrated that display both the surface patterns in the near field and designed holographic images in the far field[35–38]. Chiral LC superstructures have also been adopted to realize dynamic hybrid multiplexed holography and optical rotatory dispersion-based polychromatic holography[33,34]. In addition, inspired by the ancient Tiger Amulet, the high-level-security “four-in-one” holographic encryption is obtained via photopatterned LCs, which distribute a secret among four LC regions in the transverse plane[32]. Despite the potential to introduce a secret-sharing design, the exploration of LC holography in a tandem cascaded manner with two or more secret keys has remained elusive, constrained by traditional LC holographic algorithms.
Here, we experimentally demonstrate a cascaded LC holography scheme that enables secret sharing between two LC elements (secret keys, namely, and ) (Fig. 1). A new holographic iterative algorithm that is simple, efficient, and suitable for various cascaded holographic devices is proposed to calculate these two phase holograms. Two independent holographic images can be achieved in the far field when and are illuminated by circularly polarized light separately. When they are carefully aligned and stacked, the cascaded LCs produce a new holographic image that varies from the images created by each individual LC key. Furthermore, we demonstrate the LC-based dynamic optical encryption scheme by applying the electric fields to two LC elements. The ciphertext can only be revealed by applying the correct voltage keys. This strategy proves to be highly efficient in situations where different ciphertexts need to be transmitted to multiple recipients. This work may provide a dynamic secret-sharing LC platform, offering unique advantages such as enhanced security through multilayered holographic encoding and more complex reconstruction processes.
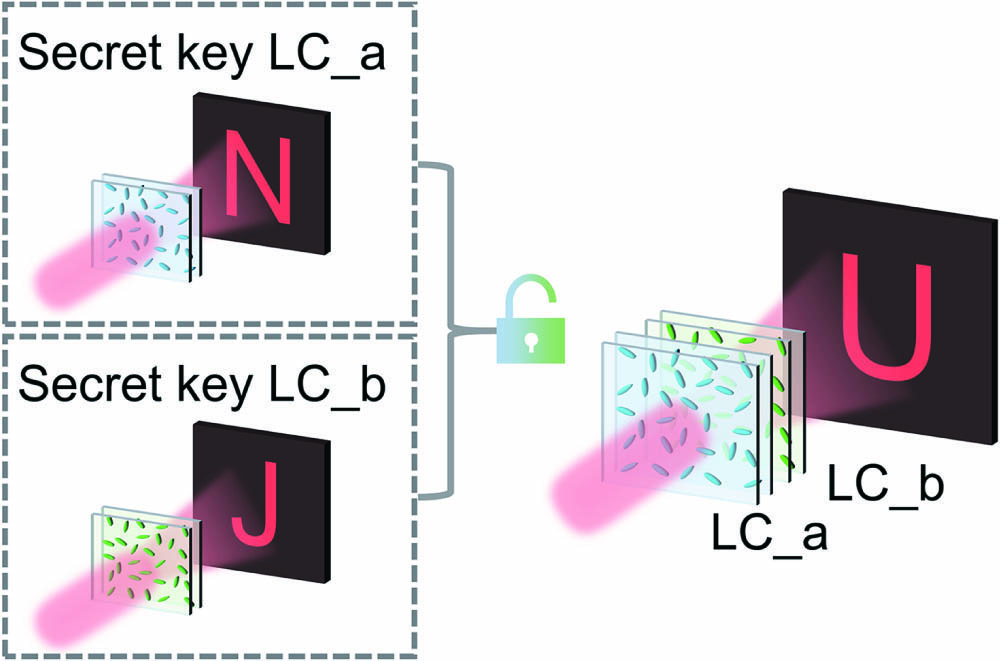
Fig. 1. Schematic illustration depicting the conceptual implementation of the cascaded LC holographic encryption. Three independent holographic images are reconstructed with LC_a, LC_b, and cascaded LC_a and LC_b.
2. Principle
The geometric phase in anisotropic LCs is an intriguing phenomenon. During the geometric phase modulation process, the incident circular polarization is handedness-converted, and the transmitted light carries a space-variant phase factor called the geometric phase [also known as the Pancharatnam–Berry (PB) phase[43,44]], twice the value of the azimuthal orientation distribution of LC . Conjugated phases are encoded for opposite circularly polarized light. Thus, the phase modulation by LCs can be expressed by , i.e., for circular polarizations: , , where and stand for the right-handed and left-handed circular polarizations.
Our design is to use two LC elements ( and ) as the secret keys for holographic encryption. These two LC elements are encoded with two different phase holograms, and , which allows them to reconstruct two independent holographic images in the far field under the illumination of circularly polarized light (two channels). By cascading these two LC elements in a tandem manner, the light is modulated by the accumulated phase retardations of both and , and a new cascaded holographic image is created. Specifically, for the single-LC-layer mode, the incident right-handed circularly polarized (RCP) light passing through the () will be converted to the opposite circular handedness and modulated by the geometric phase (). In the cascaded LC (tandem) mode, the two LC elements are tightly stacked. The incident RCP light will be converted to left-handed circularly polarized (LCP) light after transmitting through and accumulate the phase delay of . Then, the light is converted back to RCP and accumulates the total phase retardations of both layers and : after transmitting through . We aim to accomplish the independent encoding of the phase holograms and to two LC secret keys, and further introduce an additional channel [] for displaying a new holographic image, each of which can be custom-designed. Here, the holographic image encoded by the third channel can be regarded as the encrypted information, which is shared by two LC secret keys.
From the expression , it seems these three channels have a certain level of cross talk, which appears to be in conflict over the notion of independent encoding of single LC and cascaded LC holographic images. However, the independent engineering of these three channels is still possible (verified experimentally). First, in our design, only the intensity distribution of the far-field holographic image is paid attention to, with no imposition of direct restrictions on the phase distribution of the holographic image in the far field. This consequently allows for a certain level of flexibility in the design of three holographic images. Second, the fixed phase hologram corresponds to multiple combinations of and , which induces the other degree of freedom. For example, the phase combinations of (, ) and (, ) produce the same phase holograms , where is an arbitrary value. These degrees of freedom contribute to the independent design of , , and .
The hologram algorithm serves as a pivotal aspect in realizing the above design. Conventional LC holographic algorithms are usually one-layer solutions for multifunctional holography. It is challenging to achieve two independent phase holograms for physically separate LC layers that can reconstruct their respective holographic images as well as a third new holographic image when they are cascaded. Based on the quantified relation of , we propose a modified Gerchberg–Saxton algorithm to encode different holographic images (“N,” “J,” and “U”) onto three channels (, , and ). Our algorithm is essentially a phase-retrieval algorithm that can simultaneously calculate and for the two LC secret keys. The resultant , , and will correspond to the generations of holographic image a, image b, and image c (“N,” “J,” and “U”) in the far field.
Figure 2(a) shows the flow chart of our algorithm, which consists of two iterative loops. Here, fast Fourier transform (FFT) and inverse fast Fourier transform (iFFT) are used for constructing iterative loops between the holographic images in the far field and the hologram in the near field. Because of the standard Gaussian beam used to illuminate the cascaded LC elements, a Gaussian distribution () is used for the replacement of the amplitude in the near field. The first iterative loop is represented by the red part of the flow chart. We input a random phase at the beginning of the iterative loop. The target image c is used for the replacement of the amplitude in the far field, which only participates in the first loop. Then a feedback can be obtained through iFFT back to the near field, which can improve the convergence speed. After obtaining the desired phase distribution by sufficient iterations in the first loop, is adopted in the next iterative loop indicated by blue and green colors to calculate the phase distributions of and . The equations of and are used to connect the two parts of the second iterative algorithm and the calculated by the first iterative loop. It is worth noting that the participation of image a, image b, and quantitative relationships ( and ) cause the convergence of the second iterative loop towards a direction, where , and can well reconstruct the holographic images of “N,” “J,” and “U” in the far field, respectively. After a sufficient number of iterations, we obtain the optimized phase distributions and [Fig. 2(b)]. Corresponding director distributions of and can be calculated according to .
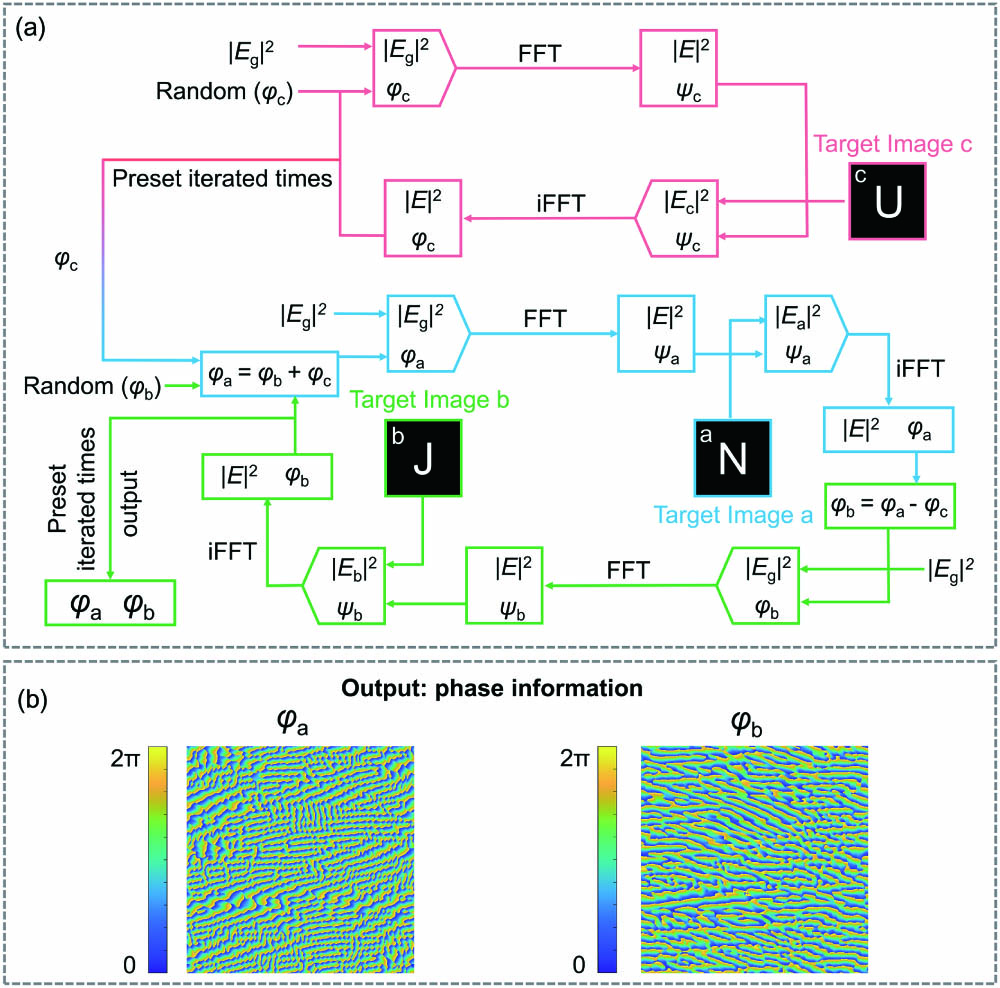
Fig. 2. Flow chart of the iterative algorithm with the calculated LC phase holograms. (a) Modified Gerchberg–Saxton algorithm. Fast Fourier transform and inverse fast Fourier transform are denoted as FFT and iFFT. The red, blue, and green parts of the flow chart represent the parts involved in the generation of phase profiles of φc, φa, and φb. |Eg|2 corresponds to the amplitude of a standard Gaussian beam. (b) Output phase information for LC elements (LC_a and LC_b).
3. Experiments
3.1. Materials and methods
In our experiment, a commercial nematic LC E7 (Jiangsu Hecheng Display Technology Co., Ltd., China) was utilized for fabricating LC holographic elements. Two glass substrates were assembled to form an LC cell. SD1 (Nanjing Ningcui Optical Technology Co., Ltd.), employed as the photoalignment agent, was dissolved in dimethylformamide at a concentration of 0.35% (mass fraction) (Note 1 in Supplementary Material). After ultrasonic and UV-ozone cleaning procedures, glass substrates () coated with indium tin oxide (ITO) underwent a spin-coating process using the SD1 solution[33,34,40,45,46]. Following this step, the substrates were transferred to a hot stage and subjected to a curing process at 100°C for a duration of 10 min. To ensure the desired cell gap, two substrates were separated by a mixture of spacer and epoxy glue, resulting in a measured cell gap of 4.5 µm.
The phase holograms were generated by our modified Gerchberg–Saxton algorithm. The director distribution is calculated according to . Then, we conducted the photopatterning process. The empty LC cell was positioned at the image plane of a digital micromirror device-based microlithography system[40,46,47]. Through a multistep, partly overlapping, exposure process with synchronous polarization control, we recorded the designed pattern of LC director distribution to the alignment layer. Specifically, the calculated director distribution, ranging from 0 to , was divided into 36 equally sized subregions. Each subregion was assigned a uniform director value, ranging from to , with an interval of . A sum region, consisting of five adjacent subregions, was exposed simultaneously with a certain intensity and an exposure time of 3 s. However, these conditions were not sufficient to induce a stable reorientation of SD1. Subsequently, the sum region was exposed again, shifting one subregion at a time, while the polarizer rotated synchronously by 5°, which is 180°/36. This process was repeated until each subregion was exposed 5 times, resulting in a total exposure time of 15 s, which effectively oriented the SD1 molecules according to the designed . The target LC microstructure comprises . The nematic LC E7 (Jiangsu Hecheng Display Technology Co., Ltd., China) was then capillary-filled into the photopatterned cell at a temperature of 80°C. The cell was slowly cooled to room temperature, ultimately leading to the formation of holographic LC elements. Characterizations are described in Note 2 (Supplementary Material).
3.2. Experimental results
Figures 3 and 4 showcase the characterization of cascaded LC holographic encryption. We depict the experimental setup in Fig. 3(a). A linear polarizer and a quarter-wave plate are strategically placed before the LC elements to achieve the RCP for incidence. Figure 3(b) shows the calculated LC director distributions and of and . Then, the two LC elements are photopatterned according to and using the homemade high-precision photoalignment technique (see details in Section 3.1). Polarization optical microscope (POM) images of central enlarged regions of the two LC elements are captured, exhibiting high-quality architectures with striped textures consistent with their respective director distributions. Then, and are placed individually (single-layer mode) or simultaneously (cascaded-layer mode) in the optical path to carry out the holographic displays. A high sensitivity of the alignment of these two LC elements is anticipated. We fix the position of while carefully adjusting pixelwise within the transverse plane using a high-precision displacement stage, until obtaining the encrypted cascaded holographic image.
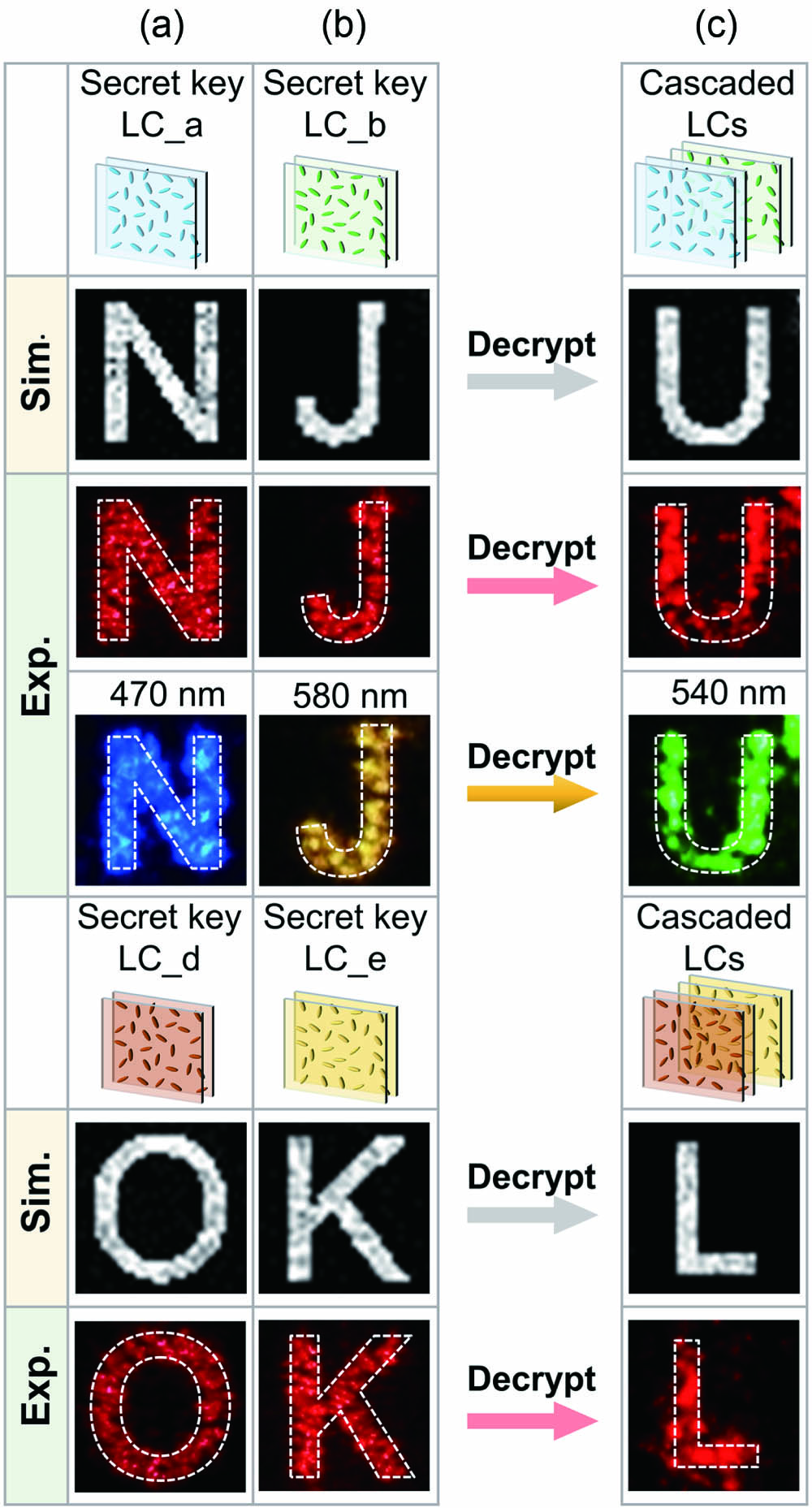
Fig. 4. Theoretically and experimentally reconstructed holographic images of letters “N,” “J,” “U,” “O,” “K,” and “L” for cascaded holographic encryption. (a), (b) Reconstructed holographic images (letters “N” and “J” from LC_a and LC_b, and letters “O” and “K” from LC_d and LC_e) in the single-LC framework; (c) holographic images of letters “U” and “L” in the cascaded LC framework. These images are marked by white dotted lines.
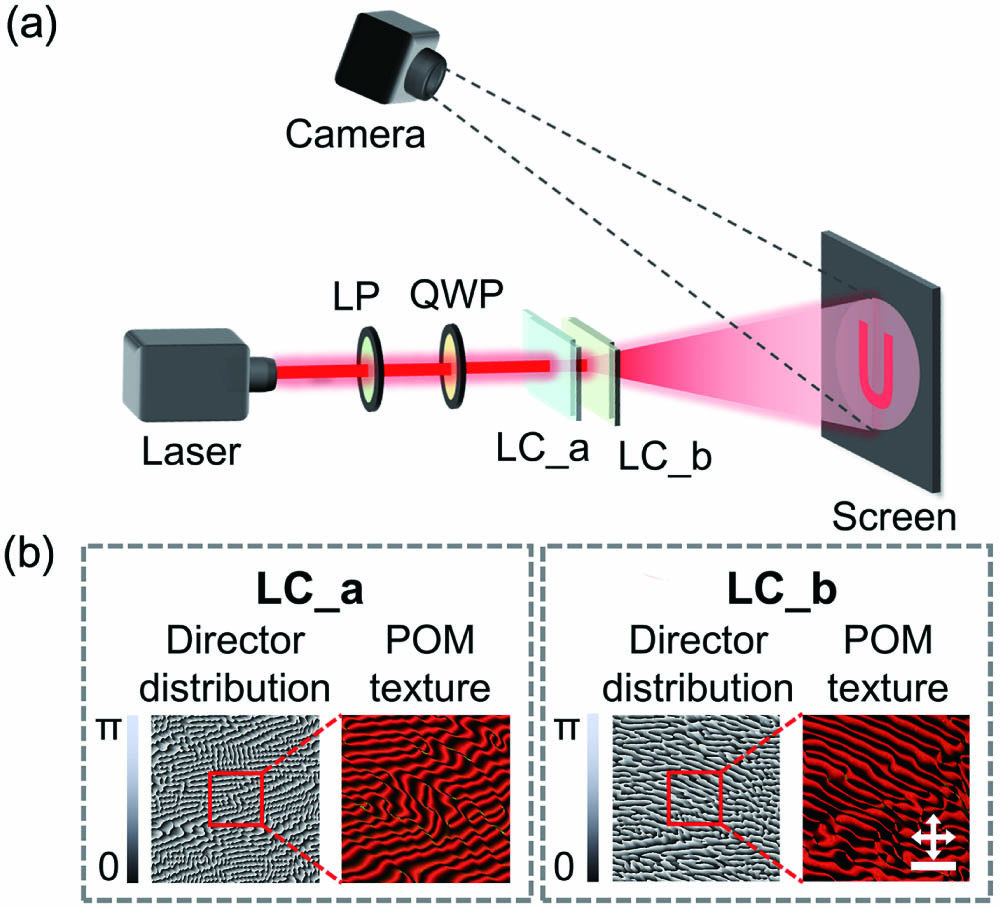
Fig. 3. Experimental setup and two LC elements (LC_a and LC_b) for secret sharing. (a) Experimental setup to record the holographic images. The optical path contains either one LC element or both the LC_a and LC_b. LP, linear polarizer; QWP, quarter-wave plate. (b) Designed phase profile of LC director distributions and the crossed polarized microscopic textures of LC_a and LC_b; the orthogonal polarizer and analyzer are represented by crossed white arrows. Scale bar: 75 µm.
As illustrated in Figs. 4(a) and 4(b), when illuminated by circularly polarized light at a wavelength of 633 nm, the two phase holograms of and successfully reconstruct high-quality target holographic images of the letters “N” and “J” in the far field, respectively, with little background noise. In the cascaded mode, the close stacking of two LC elements along the propagation direction results in the decryption of the holographic image of the letter “U” [Fig. 4(c)]. The above experimental results agree well with the simulated holographic images in the second row. In comparison to the single-LC mode, the holographic image in the cascaded-LC mode exhibits slight noise. It is worth noting that each LC element consists of two glass substrates and a photopatterned LC layer between the two substrates, implying an inevitable distance between the two LC layers (the thickness of two substrates: ). While the algorithm does not take into account the factor of light propagation between and , this may be attributed to such noise. In addition, the slightly mismatched alignment between these two LC secret keys may influence the quality of the cascaded holographic image. These factors can be further improved either by incorporating a propagation function into the algorithm (Fig. S1 in Supplementary Material), or adopting microstructured LC polymers as the secret keys, or conducting a more rigorous experimental procedure. Broadband holographic performances (at 470, 580, and 540 nm) are also demonstrated. Holograms implemented with different wavelengths exhibit different sizes of the holographic images[47]. Moreover, we found that the wavelength difference also has an impact on the efficiency of polarization conversion of the geometric phase, thus affecting the holographic efficiency. This is determined by the half-wave condition = mπ, where represents the birefringence of the LC, is the thickness of the LC layer, m is an arbitrary integer, and is the wavelength.
To further demonstrate the arbitrary design of holographic images for the three independent channels, we also fabricate secret keys of LC_d and LC_e (Fig. S2 in Supplementary Material) and demonstrate their holographic encryption capability. As shown in Fig. 4, all the holographic images (“O,” “K,” and “L”) reconstructed in the single-LC and cascaded-LC frameworks conform to the expected outcomes. The holographic images of “O” and “K” do not leak any information of the ciphertext “L”, implying an effective, flexible, and highly secure encryption scheme of optical information in the cascaded channel. This is also important in applications such as optical data storage, communication networks, and anti-counterfeiting measures.
Based on the LC holographic performance in the cascaded LC mode, we further highlight the dynamic cascaded LC holographic encryption by taking advantage of the remarkable electro-optical tunability of LCs. The basic principle is rooted in the electrically controlled reorientation of LC molecules. As depicted in Fig. 5(a), before we apply an electric field to the LC element, i.e., the applied voltage is at 0 V, LC molecules align parallel to the glass substrates in accordance with the underlying alignment pattern, thereby yielding an “on” state for the holographic image. The cascaded holographic information is “on” only if the two LC elements are both in the “on” states [Fig. 5(b)]. As the voltage increases, the LC molecules gradually undergo a transition to upright orientations, which are perpendicular to the substrates when the voltage reaches 14 V (1 kHz, square-wave signal). In this case, the holographic functionality of the LC hologram is disrupted, resulting in an “off” state. When both the LC elements are in the “off” states, the resulting holographic information appears blank.
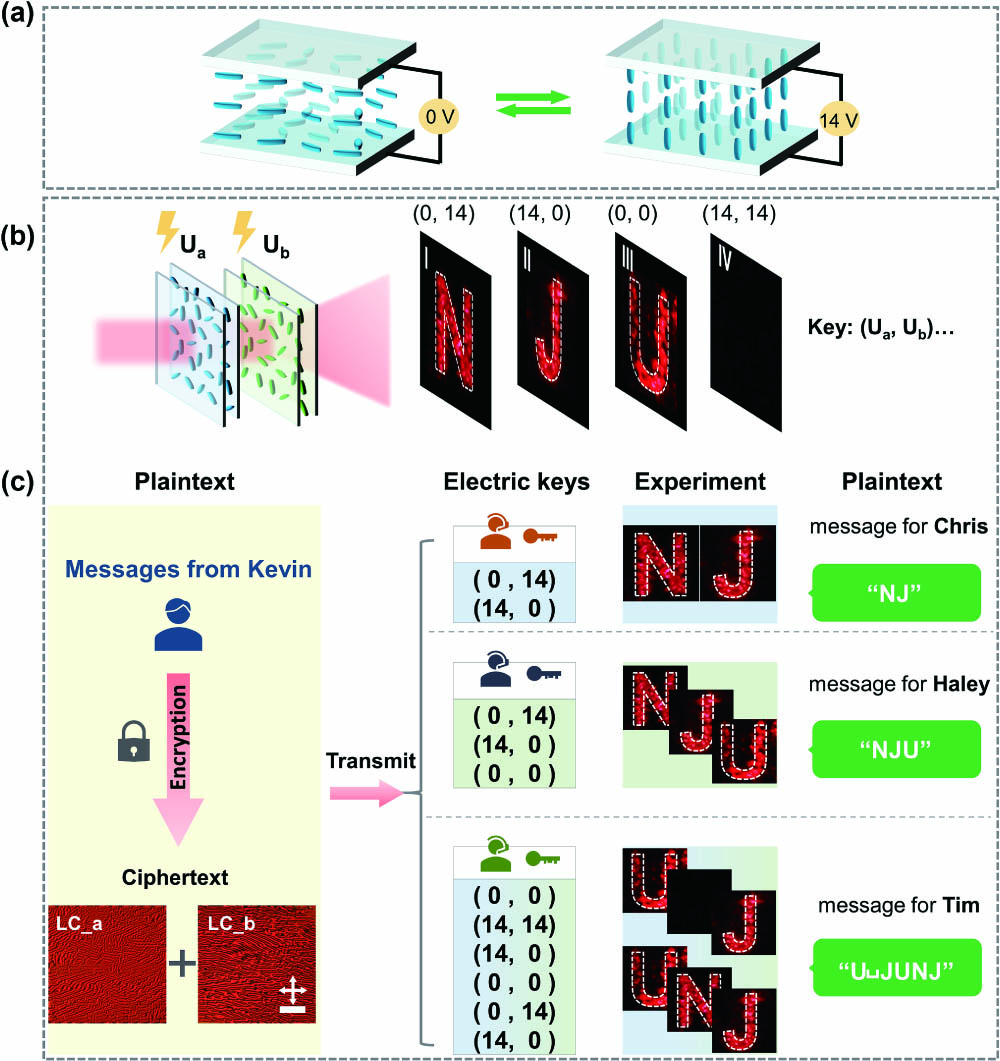
Fig. 5. Electrically dynamic optical encryption based on cascaded LC holography. (a) Schematic illustration of the electric switching of LC hologram with different applied voltages (0 V and 14 V); (b) four basic holographic images in the cascaded LC framework with different combinations of applied voltages; (c) electrically dynamic optical encryption based on cascaded LC holography for the scenario, where ciphers or passwords are sent to multiple receivers. Scale bar: 250 µm.
The ability to electrically program both and permits advanced optical information processing and encryption. We define a coding rule that each cipher corresponds to a combination of applied voltages to the cascaded LC elements, which acts as the private key. By sequentially switching the LC elements according to the key, the receiver can decrypt and safely receive the message. For instance, the key of {1. (14, 0); 2. (0, 0)} can decrypt the message of “JU.” With any other key, incorrect information will be obtained.
Following the above rule, we present a robust, dynamic, secure method for optical encryption and decryption utilizing the dynamic cascaded LC holography. As illustrated in Fig. 5(c), Kevin would like to send different ciphers or passwords to multiple receivers, including Chris, Haley, Tim, and so on. These messages are all encrypted and shared in and . Each receiver is provided with the two LC elements and is informed of the customized decryption key. Chris gets the key {1. (0, 14); 2. (14, 0)} and then obtains the reconstructed holographic image of “NJ.” Thus, she reads out the message of “NJ,” which is abbreviated from Nanjing. Similarly, Haley receives the ciphertext of “NJU,” which is the abbreviation for Nanjing University. Furthermore, the encryption key can be programmed to incorporate more complex voltage combinations. For example, Tim first applies (0, 0) to obtain the letter “U”; then he uses (14, 14) and reads out a blank space. “J,” “U,” “N,” and “J” are sequentially obtained according to the following voltages {3. (14, 0); 4. (0, 0); 5. (0, 14); 6. (14, 0)}. Therefore, he receives the password “U˽JUNJ.” Other receivers can also decode their respective message by the provided keys. This dynamic cascaded encryption scheme allows for obtaining arbitrarily and nearly unlimited encoding capabilities (passwords such as N˽UJJJUNJ˽˽UJJN˽N) from the holographic images by providing customized voltage keys. This indicates an enhanced holographic encryption technique, holding great potential in large-capacity optical cryptography with multiple receivers.
4. Discussion
The new aspect of the current work is mainly the LC implementation of cascaded holography for optical encryption. A modified Gerchberg–Saxton algorithm is proposed to calculate the LC holograms for secret sharing. The encrypted cipher or password can only be read out with cascaded LCs. Notably, the cascaded LC configuration plays a crucial role in optical encryption, as it incorporates an independent and physically separated secret-sharing design, thereby enabling a higher level of security in optical encryption[23–25]. Without the proper cascaded procedure of these secret keys, incorrect or misleading information can be obtained. The conversion efficiency of cross-polarization is another important parameter, which is determined by the half-wave condition. When the LC element satisfies the half-wave condition, the efficiency of LC-holographic performance is maximized. Any deviation from the half-wave condition will result in a decrease in efficiency. By leveraging the electro-optical tunability of LCs, we further create a dynamic cascaded LC platform for advanced optical encryption. This is achieved through the reprogramming of applied electric signals to two cascaded LC elements. A typical encryption scenario is proposed where Kevin transmits different passwords to multiple receivers. This strategy adds more dimensions of complexity to the optical encryption process.
This cascaded LC holography offers an enhanced level of security through the implementation of dual-layered holographic encryption. Actually, more adjustable parameters can be leveraged in the design of an optical encryption system. These parameters include the number of LC elements, lateral displacement of and distance between adjacent LC elements, parameters of external stimuli, diffraction angle, etc. These additional parameters can significantly impede unauthorized access or decryption. Additionally, the tunable nature of LCs allows for the flexible and dynamic manipulation of holographic performance, establishing a dynamic secret-sharing platform. Further incorporation of both the applied voltage and frequency of the electric field or light field will enable potentially high-speed information processing and real-time complex encryption schemes. Third, this work can be extended to diversified LC systems (such as cholesteric LCs and blue-phase LCs). We can anticipate more alluring optical multiplexing systems with well-designed broadband reflective and polychromatic features for future advanced optical encryption systems.
The experimental demonstration of cascaded LC holography in this study highlights its potential in both cascaded optical encryption with secret sharing and electrically dynamic optical encryption with unlimited encoding capabilities. The utilization of more than one LC layer, the cascaded configuration, and the high-quality holographic images offer enhanced security, flexibility, and potential applications in various fields, such as visual optical cryptography, optical communications, anti-counterfeiting measures, optical data storage, dynamic holographic display, all-optical computing, and diffractive neural networks.
Article Outline
Zeyu Wang, Han Zhang, Xiaoheng Liu, Yunjie Dou, Wei Duan, Wei Chen, Lingling Ma, Yanqing Lu. Cascaded liquid crystal holography for optical encryption[J]. Chinese Optics Letters, 2023, 21(12): 120003.





